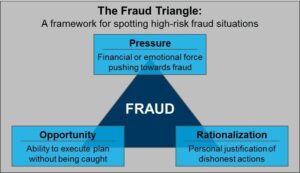
The reality of workplace theft hits businesses hard. Companies lose $50 billion to employee theft each year, and this creates a huge financial strain on organizations regardless of their size. Studies show that 75% of employees steal from their workplace at least once. Nearly two-thirds of businesses have fallen victim to employee theft.
Business owners face some scary numbers. The Association of Certified Fraud Examiners reports that companies lose roughly 5% of their yearly revenue to fraud. An average fraud case costs businesses $1.5 million. The “10-80-10 rule” makes things even more concerning – 10% of people stay ethical no matter what, 80% might steal given the right situation, and 10% will steal any chance they get. Businesses need strong fraud prevention strategies to survive. Employee theft makes up almost half of all inventory shrinkage. Companies can protect their assets and keep their finances healthy by spotting the hidden signs of potential fraud early.
Unusual Changes in Employee Lifestyle
Image Source: Fraud.com
Employees who show lifestyle changes that don’t match their known income often raise red flags for workplace fraud. These discrepancies serve as early warning signs of employee theft.
What this sign means
An employee’s lifestyle changes become apparent when they display wealth that doesn’t match their salary. They might buy luxury cars, go on expensive vacations, or wear designer clothing without any clear extra income sources [1]. The pattern raises eyebrows when someone shows up in a $100,000 vehicle earning $75,000 annually[1]. Their behavior often changes too. They might get defensive about money questions, refuse to share their work, or resist taking time off [1].
Why it may indicate employee fraud
Sudden lifestyle improvements without matching salary increases suggest employees might be padding their income through fraud [2]. The link between unexplained wealth and possible fraud exists because:
- People who steal from work often show off their illegal gains through visible purchases
- Their financial stress goes down as they steal more, which leads to bolder spending
- Research shows companies can cut losses by if they catch these warning signs early up to 60%[3]
David Tyree, a senior advisor and retired DEA agent, puts it well: “Fraudsters count on people trusting them… When someone regularly overrides internal controls, it’s not just a red flag—it’s a siren” [3].
How to break down lifestyle red flags
Experts suggest using lifestyle analysis to learn about an employee’s spending habits, social activities, and overall expenses compared to their reported income [2]. This process has sections on:
- Monitoring spending patterns – Look for big purchases and luxury items that don’t match known income
- Analyzing social media profiles – Social platforms reveal spending habits and lifestyle differences
- Linking lifestyle to potential fraud – Use observed behaviors to build stronger legal cases [2]
Companies should be careful during this process. Sometimes people come into money legitimately through inheritances or side businesses [2]. Organizations need proper investigation protocols before making any accusations. Setting up whistleblower hotlines helps since tips lead to fraud discovery 47% of the time [4].
Organizations can spot potential fraud early by watching for lifestyle differences carefully. This approach helps them minimize financial losses and recover assets effectively.
Frequent Complaints About Pay or Recognition
Image Source: Employ Borderless
Forensic accountants closely watch employee complaints about pay and recognition as warning signs of possible workplace fraud. These vocal signs of unhappiness might look normal, but they often point to bigger problems ahead.
What this sign means
Employee complaints about pay usually show up as ongoing feelings of being undervalued, underpaid, or mistreated at work. These grievances often look like:
- Baseless complaints about working conditions
- Getting defensive about work activities
- Too much focus on comparing pay with coworkers
- Getting upset during money-related discussions
Unlike sudden lifestyle changes, pay complaints show how employees see unfairness rather than visible signs of new wealth. These complaints might be real or could act as shields against possible discipline [5].
Why it may indicate employee theft
Job dissatisfaction ranks among the biggest reasons for employee fraud. Research shows that or underpaid are more likely to justify stealing dissatisfied workers feeling undervalued[6]. This happens because:
- Money pressure creates the first push toward theft
- Feeling treated unfairly helps employees justify wrong actions
- Believing they’re underpaid makes people feel entitled
Studies confirm that job satisfaction directly affects unethical behavior [7]. The Gallup State of the American Workforce report shows that U.S. businesses between $483 billion to $605 billion each year in lost productivity actively disengaged employees cost[7].
How to address it proactively
Forensic accountants suggest several ways to reduce risks from compensation complaints:
- Early HR involvement – HR professionals should step in as soon as pay complaints start to check for real legal issues [5]
- Documentation protocols – Keep detailed records of all pay discussions without doing anything that might look like retaliation
- Regular access audits – Review systems regularly to ensure employee access matches their job duties [7]
- Ethical culture reinforcement – Build stronger accountability and ethical values in both office and remote work settings [8]
Companies need to handle these complaints carefully since wrong moves could lead to wrongful termination lawsuits. A single complaint might also point to bigger compliance problems, especially with gender pay gaps or overtime rules [5].
Reluctance to Take Time Off
Image Source: Commonwealth Fraud Prevention Center
You might think an employee who never takes vacation is just a hard worker. But this behavior is actually one of the most telling warning signs of fraud. Fraud investigators consider this pattern a red flag that needs immediate attention.
What this sign means
An employee might be hiding something if they never use their vacation days or take sick leave. They work long hours, coming in early and staying late. These people often make excuses to avoid time off and don’t want to share their work. They might insist on delaying tasks until they return. The biggest problem is that they keep total control of specific financial processes, making themselves seem essential to daily operations.
Why it may indicate hidden fraud schemes
This behavior pattern relates directly to hiding fraudulent activities. Employees who steal or embezzle avoid taking time off because:
- They need to be there to manipulate records, answer questions, and avoid getting caught [9]
- Someone else doing their job might spot problems, even during brief absences [10]
- They need constant access to financial systems to hide what they’re doing [10]
The Association of Certified Fraud Examiners found something interesting. Companies that require employees to take vacations saw fraud losses drop by 50% [link_2] [11]. The Federal Deposit Insurance Corporation has backed this approach since 1995, recommending at least two weeks of mandatory vacation [11].
How to enforce mandatory vacations
To make vacation policies work, you need:
- Well-laid-out absence requirements – Your team should take vacations in week-long blocks instead of random days [11]
- Cross-training protocols – Other employees should handle the work while someone is away rather than letting it pile up [11]
- System access restrictions – Remove remote access during vacation time to prevent secret work [11]
- Compliance monitoring – Someone must track vacation use and make sure everyone follows the rules [11]
Mandatory vacations serve two purposes. They help spot existing fraud when replacements notice something odd. They also discourage potential fraud because people know someone else will do their job. All the same, fraud investigators know that required vacations can’t stop all fraud, especially when you have employees working together to hide it. That’s why we need detailed fraud prevention strategies [11].
Excessive Control Over Financial Processes
Image Source: Fraud.com
A major red flag in fraud detection shows up when employees keep an unusually tight grip on specific financial processes. This behavior pattern serves as a basic element in major embezzlement schemes, according to forensic accountants.
What this sign means
Several observable behaviors point to excessive control. Employees who insist on handling all financial transactions without sharing responsibilities raise concerns. They push back against changes to procedures and resist improvements to existing workflows [12]. These people usually deny oversight, keep exclusive access to financial records, and say no to technology upgrades that could make things more transparent [1]. Many organizations find this warning sign after fraud has already taken place. Companies have suffered median fraud losses amounting to 5% of annual revenue[3].
Why it may indicate embezzlement risk
This behavior pattern links directly to embezzlement because concentrated control creates perfect conditions for fraud. The risk goes up at organizations where one person controls the whole financial process. These setups let perpetrators commit fraud and hide their tracks [13]. A person who can start, authorize, record, and review transactions without others has the power to:
- Hide unauthorized transfers by changing records [14]
- Move money to personal accounts without getting caught [14]
- Set up fake vendors or employees [14]
The Association of Certified Fraud Examiners tells us that . After discovering fraud, 82% of victim organizations changed their anti-fraud controls half of all frauds occurred due to inadequate internal controls[3].
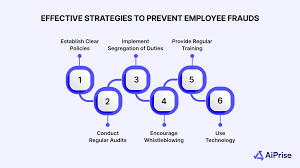
How to implement segregation of duties
Segregation of duties (SoD) stands out as the best defense against excessive control risks. This method splits up responsibilities so no single employee runs an entire process [12]. Organizations should:
- Establish process policies – Write down standard operating procedures that spell out responsibilities for each department and person [12]
- Build a segregation matrix – Create a list of all responsibilities to ensure proper distribution without conflicts [12]
- Apply role separation – Split up four major incompatible duties: authorization, custody of assets, recording transactions, and resolution [13]
Forensic accountants suggest separating specific processes for the best results. Different people should collect, deposit, record, and resolve cash receipts [12]. In purchasing, separate staff members should start orders, approve purchases, and begin payments [12]. While splitting up duties might slow things down at first, forensic accounting professionals say these controls stop much bigger problems from developing [12].
Unexplained Inventory Shortages
Image Source: MGO CPA
Organizations often discover hidden financial leaks through unexplained inventory discrepancies. Inventory needs careful monitoring since it represents one of the biggest assets on a balance sheet.
What this sign means
System records and physical counts often don’t match up, showing persistent inventory shortages. Regular audits, cycle counts, and yearly inventory checks reveal these gaps. Companies need to investigate right away when shortages exceed 2%[15]. Small accounting errors might seem harmless at first but they point to deeper problems. Here are the warning signs:
- Physical stock doesn’t match what’s recorded in the system [16]
- Physical counts lead to big adjustments [15]
- Inventory systems show questionable entries [17]
- Cost of goods sold percentages spike while sales stay the same [17]
Why it may indicate asset misappropriation
Employee fraud hits manufacturing and retail sectors hard through inventory theft. Research shows of inventory shortages internal employee theft makes up 75%[18]. This is a big deal as it means that businesses lose about 6% of their yearly revenue to inventory shrinkage [19]. Inventory fraud goes beyond simple theft and includes:
- Employees create fake vendors and redirect payments to themselves [20]
- Receiving reports get altered to hide theft [2]
- Someone writes off inventory without permission [2]
- Staff uses empty boxes during counts to create fake inventory [2]
How to improve inventory controls
Good inventory controls help prevent and detect problems. Forensic accountants suggest these measures:
Segregation of duties – Different employees should handle receiving, storing, recording, and reconciling inventory [17]
Regular physical counts – Surprise counts throughout the year work better than just one annual check [4]
Access restrictions – Staff should only access inventory systems and areas based on their job needs [21]
Real-time tracking – Barcode or RFID technology in inventory management software helps keep accurate records [17]
Documentation protocols – Clear rules should exist for receiving, storing, and recording inventory [17]
Whistleblower channels – Staff needs safe ways to report suspicious activities without fear [17]
These controls help companies reduce inventory fraud risk and optimize operations when implemented systematically.
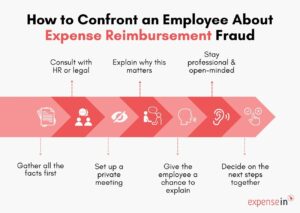
Duplicate or Altered Expense Reports
Image Source: ExpenseIn
Fraudulent expense claims often happen when employees manipulate documents. This direct attack on company finances needs forensic accountants to break down. A clear paper trail helps skilled professionals detect expense report manipulation more easily than other fraud indicators.
What this sign means
Expense report fraud shows up most commonly as duplicate submissions and document alteration. Employees submit similar receipts multiple times to create duplicate submissions, and they usually spread these across different reporting periods [22]. These duplications can take several forms:
- Claims for the same expense in January show up again in March [23]
- Corporate card charges appear as separate reimbursement requests [24]
- Expenses with slightly changed descriptions look similar [24]
- One receipt gets submitted both digitally and on paper [6]
Document alteration happens when people change dates, amounts, or details on receipts. People who commit fraud often change submission dates, time stamps, or table numbers to hide duplications [25]. Suspicious patterns need immediate attention, especially rounded numbers like USD 170.00 or USD 425.00 and expenses that consistently fall just below approval thresholds [26].
Why it may indicate reimbursement fraud
Each instance of expense reimbursement fraud costs organizations USD 33,000 on average [link_1] [27]. The Institute of Finance and Management finds that duplicate payments make up about 1.5% of a company’s outgoing cash flow [25]. These schemes succeed because controls and oversight fall short. The ACFE’s 2024 Report to the Nations shows that fraud happens due to lack of internal controls (32%), override of existing controls (19%), and insufficient management review (18%) [22].
How to audit expense claims
Companies need these systematic procedures to audit expenses effectively:
- Require original receipts and match them with submitted claims [22]
- Implement automated detection systems to flag duplicates, round numbers, and threshold-adjacent claims [26]
- Establish clear expense policies about travel, meals, and entertainment limits [22]
- Enforce approval workflows so different employees review, approve, and pay reimbursements [28]
- Conduct regular audits that focus on high-risk categories like cash purchases [29]
Businesses should use automated expense management software that applies machine learning to detect suspicious patterns while reducing false positives [27]. Regular manual audits still play a crucial role in catching subtler manipulation techniques [30].
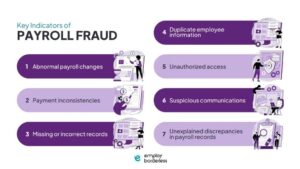
Missing or Incomplete Financial Records
Image Source: Nonprofit Leadership Center
Document irregularities give the strongest evidence of financial manipulation in workplace fraud investigations. Missing paperwork serves as a key warning sign that forensic accountants need to address right away.
What this sign means
Missing financial records show up as incomplete transaction documentation, altered invoices, or discrepancies in accounting reconciliations. The records have invoices that never made it to company books, unexplained gaps in sequential documentation, and financial statements with questionable adjustments [31]. never get picked up from printers, and these documents often contain vital financial information Approximately 30% of printed pages[32]. Record-keeping problems create real disruptions – we missed tax deadlines and faced complicated audit processes [33].
Why it may indicate accounting fraud
Fraudsters use document manipulation as their main way to hide illegal activities. They hold back evidence, give false information when asked, or create fake documentation [5]. Dishonest employees work together to show false evidence that controls work properly or make up misleading explanations for unexpected results [5]. Bad bookkeeping creates chances for dishonest employees to commit fraud or embezzlement, even in places with trusted financial staff who worked there for years [33].
How to enforce documentation policies
Organizations should take these steps to reduce documentation-related fraud risks:
- Centralized document storage – Use cloud-based systems to store all financial documentation, so nobody can claim “paperwork was lost” [32]
- Three-way matching protocols – Match purchase orders, receiving documents, and invoices before paying anything [32]
- Regular documentation audits – Review records regularly to check they are complete and accurate
- Clear retention policies – Set required timeframes to keep documentation
as strong preventive measures because employees are less likely to act dishonestly when they know someone will review their work External audits serve[31].
Unusual Vendor or Payment Activity
Image Source: Fortifai
Vendors showing suspicious activity is a vital warning sign of fraud schemes that can remain hidden for months. Most financial investigators say it takes vendor fraud average of 18 months to detect[34].
What this sign means
Unusual vendor behavior demonstrates through several red flags. These include invoices with sequential numbers and payments made at odd hours. Other signs are unusually low prices, vendors without valid tax ID numbers or proper contact details, and transactions that consistently stay just under approval limits [34]. We noticed whole-dollar amounts on invoices raise particular concerns. Sudden changes in vendor details and mismatched payment and delivery addresses are equally suspicious [35].
Why it may indicate procurement fraud
These unusual patterns often point to various scams like overbilling, fake invoicing, kickbacks, or secret deals between staff and vendors [36]. The damage goes beyond money lost – it hurts the company’s reputation and brings legal troubles while disrupting daily operations [36]. Risk and Insurance Management Society reports companies lose to procurement fraud each year between 4% to 8% of their total spending[37].
How to monitor vendor relationships
Prevention works best with proper vendor screening processes that check tax IDs and business credentials [34]. Companies should regularly audit vendor information and keep approved vendor lists. They need strict policies and approval processes that involve staff from multiple departments [34].
Accessing Data Without Authorization
Image Source: NordLayer
Forensic accountants get into unauthorized system access as a basic security threat during fraud investigations. Digital footprints help spot fraudulent activities before major losses happen, unlike physical evidence.
What this sign means
Employees show unauthorized data access when they view information beyond their job duties or permission levels. Some warning signs include system logins outside work hours, multiple failed login attempts, and sensitive data access from unknown devices [38]. On top of that, former employees with active access credentials create a major security risk [7]. Sometimes, unhappy employees try to access confidential staff information to cause harm or for their own benefit [8].
Why it may indicate data theft
Data theft often starts with unauthorized access. The Computer Fraud and Abuse Act makes it a federal crime to access protected computers without permission with intent to defraud [39]. Employees who plan to leave might download or email files in their final days to share company secrets with competitors [40]. These risks grow for companies with remote workers or BYOD policies because their devices might lack proper monitoring [41].
How to restrict and log access
To work well, access control needs role-based permissions that limit employees to information they need for their jobs [8]. Companies should:
- Use strong password policies with regular updates
- Set up multi-factor authentication
- Block users after set failed login attempts
- Watch outgoing traffic for unusual data transfers
- Run regular security checks to find weak spots [7]
Companies must quickly disable system access, cancel passwords, and take back ID cards when employees leave [7]. Regular use of these steps helps companies create strong audit trails for investigations and reduces data theft risks.
Clocking In/Out Irregularities
Image Source: Zuper
Time clock irregularities show clear signs of workplace fraud that can affect a company’s bottom line.
What this sign means
Discrepancies between recorded hours and actual work demonstrate time clock irregularities. Employees might leave early but record later departure times, arrive late while logging earlier arrival times, clock in/out for colleagues (buddy punching), or submit false timesheets [9]. Suspicious patterns also include unjustified overtime claims, repeated “forgot to punch” excuses, and time logged from unauthorized locations [42].
Why it may indicate time theft
These patterns point to time theft—a widespread form of workplace fraud that affects about 24% of workers who add an extra 4.5 hours to their weekly timesheets [43]. Companies lose up to 7% of their total annual payroll because of this practice [43]. Small discrepancies add up substantially over time. A single employee who claims just one unauthorized overtime hour each week can cost the company $1,170 per year [44].
How to use time-tracking systems
Companies can prevent time theft by using:
- Biometric verification systems with fingerprints or facial recognition to stop buddy punching [9]
- Geofencing technology that limits clock-ins to workplace boundaries [45]
- Automated alerts that tell managers about unapproved early arrivals or late departures [9]
Managers should monitor work hour patterns to spot irregularities. This approach works best when combined with clear policies and open communication with employees to maintain fairness rather than create a surveillance atmosphere [43].
Sudden Drop in Performance or Engagement
Image Source: Treasury
Poor performance at work often comes before fraudulent activities. Managers might brush off subtle behavioral changes as temporary issues, but these changes often point to deeper problems that need forensic investigation.
What this sign means
A sudden drop in performance shows up when a previously high-performing employee becomes more withdrawn. Their behavior changes show through missed deadlines, short communications, and less voluntary participation [46]. Staff members who used to actively participate may stop offering ideas, reduce interactions with coworkers, or quietly push back against new procedures. These changes usually happen slowly without obvious red flags, which makes them hard to spot without regular monitoring.
Why it may indicate internal conflict or fraud
Employees who stop participating create higher fraud risks because they can justify wrongdoing more easily [11]. These workers often bypass control procedures and follow policies less carefully when they lose their dedication to the organization [11]. Research connects low participation to more policy violations and fraud [46]. The financial effects are serious – disconnected employees hurt customer satisfaction and close fewer deals, which hurts sales [11]. They also rarely speak up about their colleagues’ misconduct, which creates an environment where unethical behavior can grow [11].
How to conduct performance reviews
Performance monitoring needs well-laid-out evaluation frameworks that use current job descriptions and clear rating definitions [47]. Performance reviews should look at specific factors including:
- Decision making and problem-solving capabilities
- Communication effectiveness with colleagues and customers
- Adherence to procedures and controls
Performance monitoring helps detect and prevent issues. Organizations can spot potential fraud indicators before major losses happen by tracking participation metrics. Regular reviews also create accountability systems that discourage fraud through increased oversight.
Unusual Transactions in Petty Cash
Image Source: HirewithEve.ai
Petty cash funds can become starting points for small theft schemes that might grow into bigger fraud operations. These funds face higher risks of misuse because they involve frequent transactions with minimal supervision.
What this sign means
Missing receipts, false expense claims, or employees leaving IOU notes instead of cash usually show problems with petty cash [48]. The warning signs include too many fund replenishments, employee checks in petty cash boxes, and unexplained cash shortages [49]. These issues might seem small but need careful investigation.
Why it may indicate skimming or theft
Small-scale petty cash fraud starts quietly when an employee “borrows” tiny amounts and leaves an IOU note [50]. The borrowed amounts grow larger over time while payback periods stretch until they stop completely [50]. Fraudsters create fake expenses with altered or copied receipts to refill the depleted funds once they reach their limits [50]. This pattern continues until someone steps in to stop it.
How to audit petty cash regularly
Random “surprise audits” throughout the year help make petty cash controls work [50]. Organizations should schedule these checks during high-risk periods like before paydays, late Fridays, or holidays [50]. Access to these funds needs strict limits, with keys given only to authorized staff [51]. The process needs detailed receipts, fund checks before replenishment, and clear limits on maximum payouts [51].
Resistance to Oversight or Audits
Image Source: Fraud.com
When forensic accountants investigate fraud, they pay special attention to employees who actively resist audit processes or financial oversight. This resistance is a major red flag.
What this sign means
Employees show resistance by deliberately withholding information or manipulating records to avoid detection [52]. They often resist procedural changes, ignore controls, or refuse to participate in audits [53]. The most common sign is their opposition to using competitive bids for goods and services [54]. This behavior creates roadblocks to maintaining financial integrity across the organization.
Why it may indicate concealment of fraud
People usually resist audits to hide embezzlement or other fraudulent activities [53]. Risk leaders who have a broad viewpoint of different departments can spot warning signs that others might miss [55]. These include reporting discrepancies and policy violations. The resistance creates ideal conditions for ongoing misconduct as fraudsters need to retain control over their schemes. Leadership must understand that management’s power to override internal controls poses an inherent fraud risk [56].
How to enforce transparency and compliance
Organizations can overcome resistance by:
- Building trust through employee education about audit benefits [52]
- Setting clear boundaries in audit charters and procedures while keeping reporting lines transparent [10]
- Conducting regular fraud prevention audits despite employee resistance
- Making change management and communication a priority to promote forward-looking mindsets [10]
The Association of Certified Fraud Examiners states that watchfulness remains the best defense against employee fraud [53]. Companies can protect themselves from major losses by encouraging team members to speak up about their concerns.
Comparison Table
| Sign of Fraud | Key Indicators | What This Means | How to Prevent and Detect |
| Unusual Changes in Employee Lifestyle | – Purchases that don’t match salary- Luxury items without clear money source- Gets defensive about money | – Shows they might be getting extra money illegally- One of the first warning signs of theft | – Watch spending patterns- Look at social media activity- Set up anonymous reporting channels |
| Regular Pay Complaints | – Always feels undervalued- Gets defensive about work- Too focused on money | – Big reason behind employee theft- Helps people justify stealing | – HR needs to step in early- Keep good records- Check access regularly |
| Won’t Take Time Off | – Doesn’t use vacation time- Avoids sick days- Works too many hours | – Needs to be there to keep fraud going- Others might spot issues during absence | – Make vacations mandatory- Train backup staff- Limit system access |
| Too Much Control Over Money | – Wants to handle everything alone- Pushes back on oversight- Won’t accept new procedures | – Makes fraud easier- Helps hide and commit fraud | – Set clear process rules- Split up duties- Create duty charts |
| Missing Inventory | – Counts don’t match records- Big adjustments after counting- Odd system entries | – Staff theft causes 75% of losses- Costs 6% of yearly revenue | – Count stock often- Control who has access- Use live tracking |
| Double/Changed Expense Claims | – Same receipt used multiple times- Changed dates/amounts- Even numbers only | – Loses $33,000 per case- Takes 1.5% of outgoing money | – Ask for original receipts- Use detection software- Audit regularly |
| Missing Money Records | – Records not complete- Unexplained blank spots- Transactions not recorded | – Common way to hide theft- Makes stealing easier | – Keep all documents in one place- Match everything three ways- Check documents often |
| Strange Vendor Behavior | – Numbers follow each other- Prices look wrong- Missing vendor details | – Points to purchase fraud- Loses 4-8% of spending | – Check vendors carefully- Audit vendors regularly- Use multiple approvals |
| Wrong Data Access | – Using systems after hours- Many failed logins- Unknown devices connecting | – Often leads to data theft- Could mean sabotage | – Set access by job role- Use two-step login- Check security often |
| Time Clock Issues | – Leaves early/comes late- Others clock in for them- Always claims overtime | – Affects 24% of workers- Wastes 7% of payroll | – Use fingerprint scanning- Track location- Set up automatic alerts |
| Work Getting Worse | – Missing deadlines- Less involved- Keeps to themselves | – Shows they might justify bad behavior- Creates room for dishonesty | – Use clear evaluation tools- Review work regularly- Watch engagement levels |
| Odd Petty Cash Use | – No receipts- Needs filling too often- IOUs in the box | – Starts small, gets bigger- Gets worse over time | – Do surprise checks- Limit who can use it- Set spending limits |
| Fights Against Checks | – Holds back information- Ignores controls- Won’t help with audits | – Trying to hide something- Lets bad behavior continue | – Clear audit steps- Regular fraud checks- Clear reporting paths |
Conclusion
Employee fraud poses a real threat to businesses of all sizes. Companies lose about 5% of their yearly revenue to fraud. This piece explores thirteen hidden signs that point to employee theft or misconduct. Business owners and managers who know these signs are better equipped to protect their assets and financial health.
Quick detection plays a vital role in keeping losses low. Warning signs like sudden lifestyle changes, tight control over finances, or staff refusing to take vacation can cut down fraud duration and its financial toll. Suspicious expense reports, inventory gaps, and unauthorized system access need immediate attention as they often reveal ongoing theft.
Prevention works better than catching fraud after it happens. Companies need reliable internal controls that include segregation of duties, required vacations, regular audits, and proper documentation. On top of that, keeping tabs on vendor relationships, time clock activities, and access privileges creates strong barriers against common fraud schemes. These measures also make it easier to spot fraud when prevention fails.
A workplace that promotes ethical behavior helps fight fraud. When companies encourage transparency, accountability, and open communication, employees feel safe to report suspicious activities. Whistleblower programs help catch fraud – tips lead to finding almost half of all cases.
Business leaders should know that no company is safe from fraud risk. All the same, knowing these warning signs and taking preventive steps reduces risk by a lot. Alert management, system reviews, and employee training work as strong deterrents against potential fraudsters.
Every business needs a full picture of fraud risks at least once a year. Control systems must adapt as operations change and new threats surface. This steadfast dedication to fraud prevention protects both finances and the company’s reputation. Fighting employee fraud takes constant alertness and the right systems working together over time.
Key Takeaways
Employee fraud costs businesses approximately 5% of annual revenue, making early detection and prevention critical for organizational survival.
- Watch for lifestyle red flags: Employees displaying wealth inconsistent with their salary often indicate supplemental income through fraudulent means.
- Implement mandatory vacation policies: Employees who refuse time off may need continuous presence to maintain fraud schemes—forced absences expose irregularities.
- Establish segregation of duties: Single employees controlling entire financial processes create ideal conditions for embezzlement and concealment.
- Monitor expense reports systematically: Duplicate submissions and altered receipts cost organizations an average of $33,000 per occurrence.
- Conduct surprise audits regularly: Unexpected inventory counts, petty cash checks, and system access reviews catch fraud before losses escalate.
- Create transparent reporting culture: Whistleblower programs detect 47% of fraud cases—employees need safe channels to report suspicious activities.
The most effective fraud prevention combines vigilant observation of behavioral warning signs with robust internal controls, regular audits, and a culture that encourages ethical behavior and transparent reporting.
FAQs
Q1. What are some common signs of employee fraud? Common signs include unusual changes in an employee’s lifestyle, reluctance to take time off, excessive control over financial processes, unexplained inventory shortages, and resistance to oversight or audits.
Q2. How can businesses prevent expense report fraud? To prevent expense report fraud, businesses should require original receipts, implement automated detection systems to flag duplicates and suspicious amounts, establish clear expense policies, and conduct regular audits of high-risk expense categories.
Q3. Why is segregation of duties important in preventing fraud? Segregation of duties is crucial because it prevents any single employee from controlling an entire financial process. This makes it more difficult to commit and conceal fraudulent activities by distributing responsibilities among multiple individuals.
Q4. How effective are mandatory vacation policies in detecting fraud? Mandatory vacation policies are highly effective in detecting fraud. They create opportunities to uncover existing schemes when other employees temporarily take over duties. Organizations implementing such policies have seen a 50% reduction in median fraudulent loss amounts.
Q5. What should a company do if they suspect employee fraud? If employee fraud is suspected, the company should document all evidence, restrict the suspected employee’s access to sensitive information and systems, consult with legal counsel, and consider engaging a forensic accountant to conduct a thorough investigation.